IT Security Consulting
Nothing is certain until it has been tested. At Spohn Consulting we offer our clients the peace of mind that comes with knowing exactly where they stand from an IT security and/or compliance viewpoint. Whether it's a basic penetration test, HIPAA audit, or a holistic security assessment, you'll find the Spohn team to be a great balance of technical expertise, friendly service, and business-minded professionalism.
Penetration Testing
Breaches cost money, time, customer confidence, and your credibility. A penetration test identifies your vulnerabilities, provides documentation for due diligence, and heightens your IT security awareness.
Our pen testing services are performed by our security engineers (i.e. white-hat hackers) utilizing advanced tools and methodologies to simulate an attack on your applications, databases, websites, servers, network devices, and computers. The goal is to determine the feasibility of a successful exploit, it's potential impact on your operations, and the financial cost to your organization.


The Difference
Some IT security vendors rely primarily on automated scanning tools to produce a report and then call that a penetration test. Our expert cybersecurity consultants know that these security scans can throw many false positives, overshadowing the more complex vulnerabilities. That's why every penetration scan we perform receives manual validation efforts to maximize the value and return on your investment. We truly desire that you be able to use the comprehensive information provided in our excellent documentation and deliverables to improve your security posture.
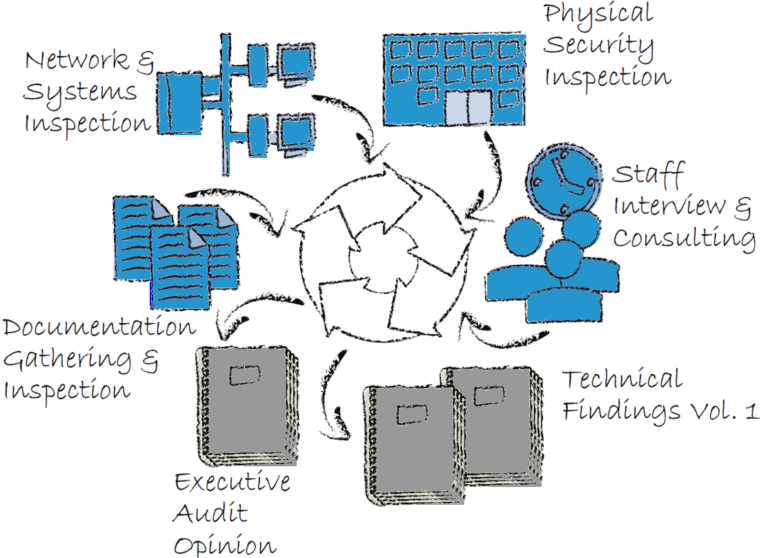
Enterprise Assessments
Find out where you stand with our holistic, in-depth enterprise security assessments. This provides you with an unbiased third-party validation, testing of your IT security posture, and prioritization of your needs.
Our experienced security engineers utilize proven tools and processes to validate physical, technical, and administrative security controls, as well as auditing your policy, plans, and procedures. Optional checklists include: NCUA, ISO/IEC 17799, Gramm-Leach-Bliley Act, FFIEC, HIPAA, HITECH, Texas Medical Privacy Law (H.B. 300) or a custom checklist built to check your own selected security controls.


Compliance Audits
Our comprehensive audit provides valuable information and support to help you meet and exceed regulatory requirements. The most popular service, our HIPAA Security Audit, results in identification of gaps in compliance with the Security Rule, identifies vulnerabilities, and provides documentation and recommendations for improvements. We validate your regulatory compliance or give you a roadmap to get there.
Business Continuity/Disaster Recovery Planning (BCDR)
Every business has risks to critical applications that could lead to potential downtime and lost productivity. Our team does the heavy lifting that is required for the creation of a comprehensive BCDR plan. This process includes a Business Impact Analysis to rank the criticality of your applications and identify the maximum tolerable downtime and data loss. Once identified, these data points will allow us to provide you recommendations on how to achieve those objectives. 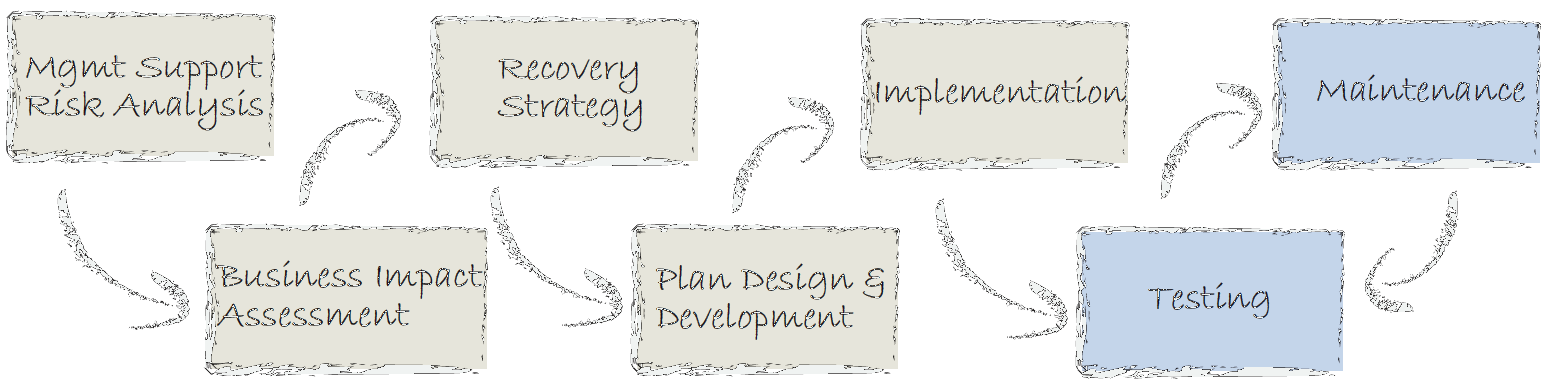 In addition, we are able to provide support for the creation of the recovery document, as well as train your staff on how to use it.
In addition, we are able to provide support for the creation of the recovery document, as well as train your staff on how to use it.
