Overview
An Enterprise Security Assessment is a comprehensive analysis of your network security against known and suspected security threats. The objective of this assessment is to identify weaknesses to improve your security posture. When performed internally, this process tends to put a strain on departmental resources and frequently competes with other high-priority projects. Our ESA service provides you all of the data you need from a third-party perspective to save internal payroll, time, and resources.
Let our experts take care of you, so your people can do what they do best.
ESA Features
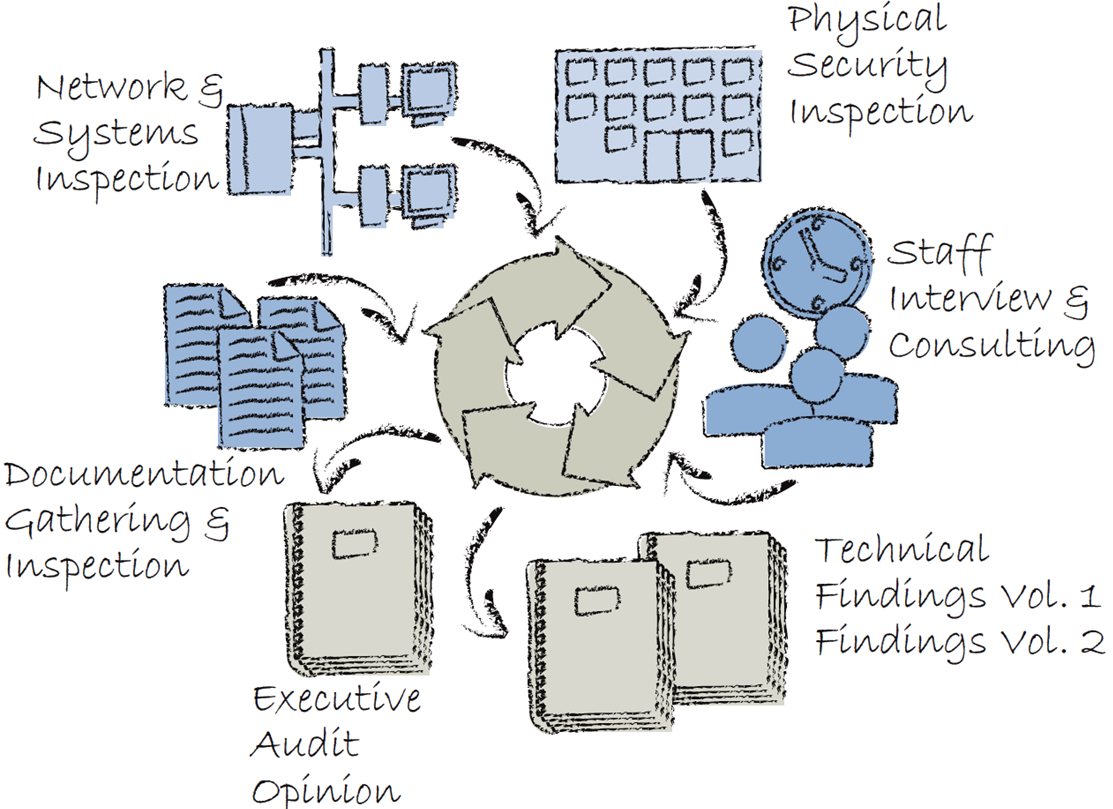
Deliverables/Documentation

Comprehensive Audit Process
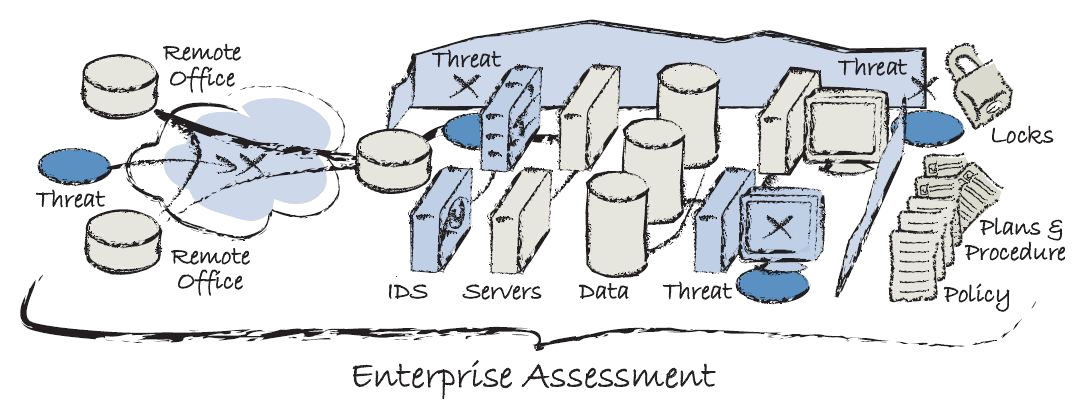
Holistic Threat Assessment
More Services Included
- Check IT inventory controls
- Assessment of firewall, router, telecom components and virus scanner
- Operations security assessment
- Review of procedures for system and log monitoring
- Review of administrative policies and procedures
- Physical security audit including lights, cameras, guards, fences
- Assess security management system
- Review organizational agreements
- Review of BCDR plan
Need More Information?
In Detail: Our Enterprise Security Risk Assessment
An audit will determine your company’s security risks and provides analysis and remedies. This provides you with an unbiased third party validation, an assessment of your security posture, and prioritization of your needs.
Our Risk Assessment employs experienced security engineers and proven tools and processes to validate physical, technical, organizational and administrative security controls, including policy, plans, and procedures.Whether motivated by the need to meet regulatory requirements ,or the desire to make better decisions to protect yourself, an Enterprise Risk Audit can be tailored to meet your needs.
Our Enterprise Security Audit has a predefined checklist of security controls to examine your entire security universe. Additional checklists include: NCUA, ISO/IEC 17799, Gramm-Leach-Bliley, Sarbanes-Oxley, FFIEC, HIPAA, HITECH, Texas Medical Privacy Law or a custom checklist built to check your selected security controls.
